Quantitative Analysis of Vulnerabilities in Cloud-Native OTA Pipelines for Software-Defined Vehicles
Vulnerabilities in Modern OTA Systems
Add bookmark
Executive Summary
The evolution of Software-Defined Vehicles (SDVs) toward continuous delivery has transformed the Over-the-Air (OTA) update pipeline from a convenient feature into a critical component of vehicle safety and security. This analysis quantifies where vulnerabilities actually concentrate in modern OTA systems, revealing that the greatest risk lies not within the vehicle’s embedded systems, but upstream - in the cloud-native infrastructure that builds, signs, and distributes software. To meet stringent regulatory requirements like UNECE R155/R156 and ISO 24089, the automotive industry must expand its security focus to harden the entire software supply chain, with particular emphasis on CI/CD orchestration, artifact management, and campaign backend services.
Introduction: The Expanding Cybersecurity Perimeter
Software-defined vehicles represent a fundamental shift in automotive architecture, relying on continuous OTA updates to deliver new features, patch vulnerabilities, and enhance performance over a vehicle’s lifespan. This shift extends the vehicle’s cybersecurity perimeter far beyond its physical boundaries, making the OTA pipeline itself a safety-relevant system. A single compromise in this pipeline can impact entire fleets simultaneously, creating a potential blast radius of unprecedented scale.
While standards such as UNECE R155/R156, ISO/SAE 21434, and the recently published ISO 24089 provide essential frameworks for secure software updates, much of the industry discourse remains qualitative. This article presents a data-driven, quantitative analysis based on mapping publicly disclosed vulnerabilities to a generalized cloud-native OTA pipeline
model. The findings provide actionable insight for engineers, security teams, and compliance officers tasked with securing the next generation of connected mobility.
Modeling the Modern OTA Pipeline
To analyze vulnerabilities consistently across different implementations, we use a six-stage model that abstracts specific technologies into core functional domains.
Table 1: Functional Stages of a Cloud-Native OTA Pipeline
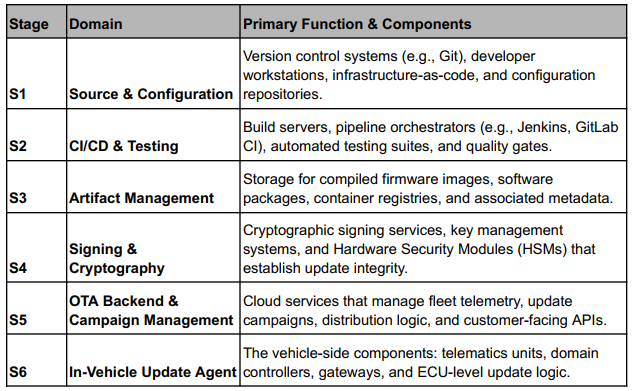
This model illustrates how software moves from development to deployment, with each stage introducing distinct security challenges.
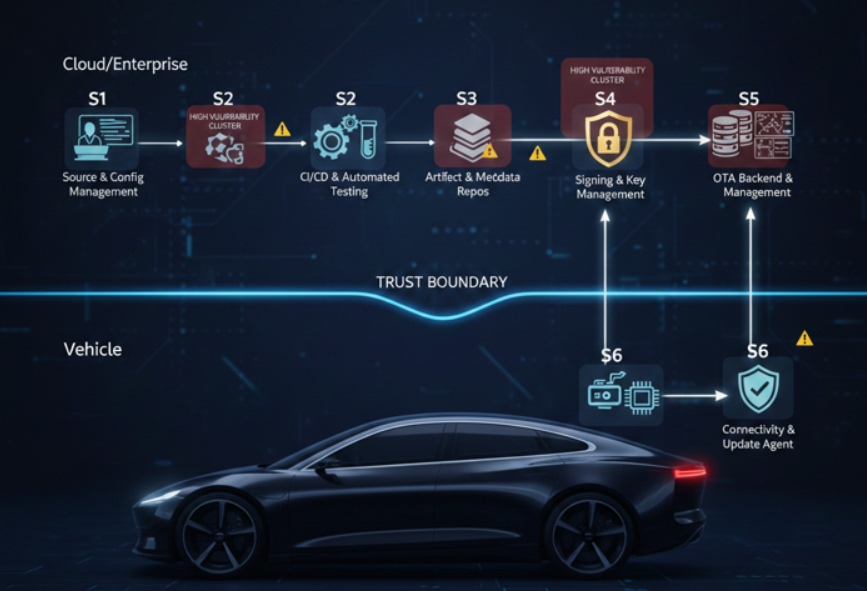
Figure 1: Visualizing the Cloud-Native OTA Pipeline, Trust Boundary, and Vulnerability Clusters.
Quantitative Findings: Vulnerability Distribution and Impact
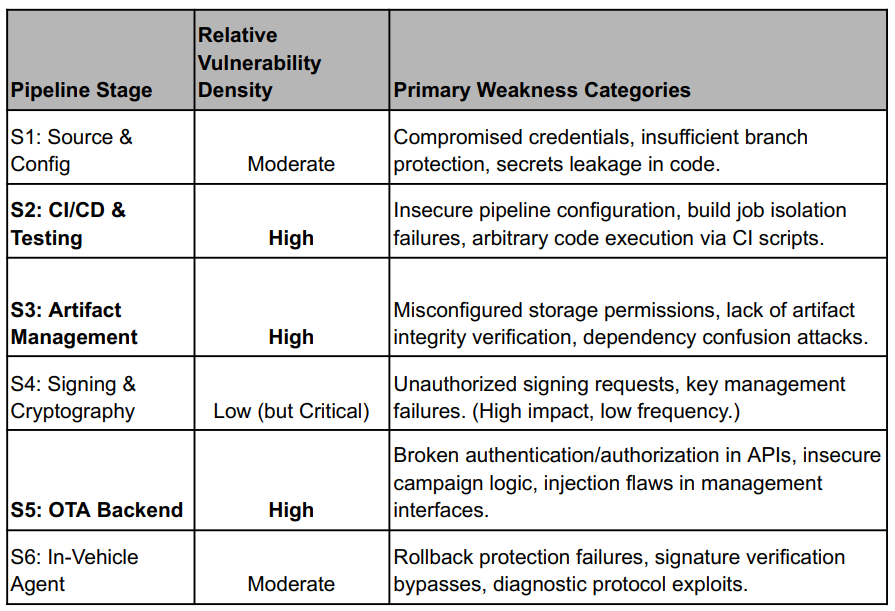
Analysis of disclosed vulnerabilities shows a pronounced clustering in the pre-vehicle cloud stages (S2, S3, S5). These environments are characterized by complex integrations, extensive automation, and numerous third-party dependencies, which collectively enlarge the attack surface far beyond that of traditional embedded systems.
Table 2: Vulnerability Density and Common Weakness Types by Stage
Interpreting Severity and Systemic Risk
A significant proportion of vulnerabilities in stages S2, S3, and S5 are rated High or Critical in common vulnerability scoring systems (e.g., CVSS). These weaknesses often enable an attacker to tamper with software artifacts or manipulate which updates are delivered to a fleet. Such compromises can render in-vehicle security mechanisms ineffective.
This highlights a crucial architectural insight: strong vehicle-side security is necessary but insufficient. If an attacker compromises the build pipeline (S2) or obtains unauthorized access to the signing service (S4), they can generate malicious firmware that passes all cryptographic checks performed by the vehicle. The trust chain is broken at its source.
Aligning with the Regulatory Landscape
Modern automotive cybersecurity is mandated, not optional. The OTA pipeline sits at the nexus of several overlapping international standards, each emphasizing different aspects of security assurance.
Table 3: Key Regulations and Standards Governing OTA Security
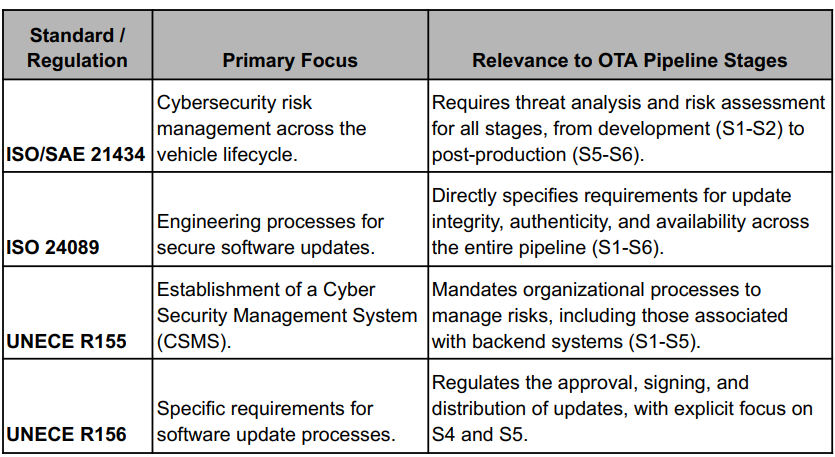
Compliance, therefore, requires demonstrating control not just over the vehicle, but over the entire software supply chain that feeds it.
Conclusion and Recommendations
A quantitative, evidence-based view of OTA pipeline security reveals a clear imperative: the automotive industry must elevate the security posture of its cloud-native development and distribution infrastructure. The highest density of exploitable vulnerabilities resides in CI/CD systems, artifact repositories, and OTA backend services - areas sometimes treated as "IT"rather than "safety-critical" concerns.
To mitigate this systemic risk, organizations should:
- Extend Security Left: Integrate automotive-grade security tooling (SAST, SCA, SBOM generation) directly into CI/CD pipelines (S2) to catch vulnerabilities before artifacts are created.
- Harden Trust Anchors: Implement strict access controls, auditing, and multi-party authorization for cryptographic signing services (S4), treating them as high-value attack targets.
- Adopt Zero-Trust for Artifacts: Enforce mandatory integrity verification and
rovenance checking for all artifacts in transit and at rest (S3), moving beyond simple storage security. - Map Controls to Stages: Explicitly map cybersecurity controls from standards like ISO
21434 and ISO 24089 to each stage of the OTA pipeline model, ensuring comprehensive coverage for audits.
By grounding security strategy in empirical data, SDV stakeholders can prioritize investments more effectively, build more resilient systems, and confidently demonstrate compliance in an era of software-defined mobility.
References
- ISO/SAE 21434:2021 – Road vehicles — Cybersecurity engineering.
- ISO 24089:2023 – Road vehicles — Software update engineering.
- UNECE Regulation No. 155 – Uniform provisions concerning the approval of vehicles with regards to cybersecurity and cybersecurity management system.
- UNECE Regulation No. 156 – Uniform provisions concerning the approval of vehicles with regards to software update and software update management system.
- Petit, J., & Shladover, S. E. (2014). Potential Cyberattacks on Automated Vehicles. IEEE Transactions on Intelligent Transportation Systems.
- Cloud Native Computing Foundation (CNCF). Software Supply Chain Best Practices White Paper.
- Upstream Security. Global Automotive Cybersecurity Report (2024 Edition).