Cybersecurity Challenges in the Era of SDVs
Increased connectivity, complexity, and attack surfaces.
Add bookmark
The automotive industry is experiencing a monumental shift from hardware-centric vehicles to Software-Defined Vehicles (SDVs). This shift enables new revenue models, enhanced safety features, and remote capabilities such as over-the-air updates and predictive maintenance. However, this technological advancement also invites new cybersecurity challenges due to increased connectivity, complexity, and attack surfaces.
SDV Architecture & Cybersecurity Landscape
SDVs integrate centralized compute platforms, virtualized environments, cloud APIs, and high-bandwidth communication protocols. Unlike traditional vehicles with isolated ECUs, SDVs depend heavily on interconnected systems, making them more vulnerable to attacks. Moreover, the adoption of third-party applications, open-source libraries, and remote diagnostics introduces significant risk vectors.
Key Cyber Threat Vectors in SDVs
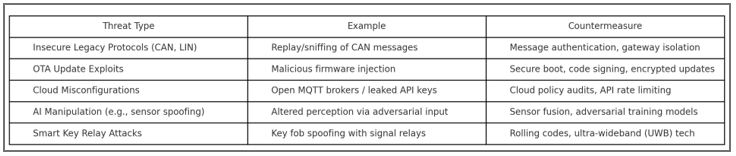
The threat landscape for SDVs includes, but is not limited to:
- Insecure legacy vehicle protocols such as CAN and LIN, vulnerable to sniffing and replay attacks.
- Attack surfaces exposed by OTA updates, Bluetooth, Wi-Fi, and mobile app integrations.
- Cloud misconfigurations, such as open MQTT brokers and API leaks.
- AI-based adversarial attacks on camera sensors, radar, and control algorithms.
- Smart key system breaches via relay and spoofing attacks.
The diagram below illustrates how SDVs increase the cybersecurity attack surface by integrating multiple interconnected domains and interfaces such as cloud, OTA, mobile APIs, and legacy protocols.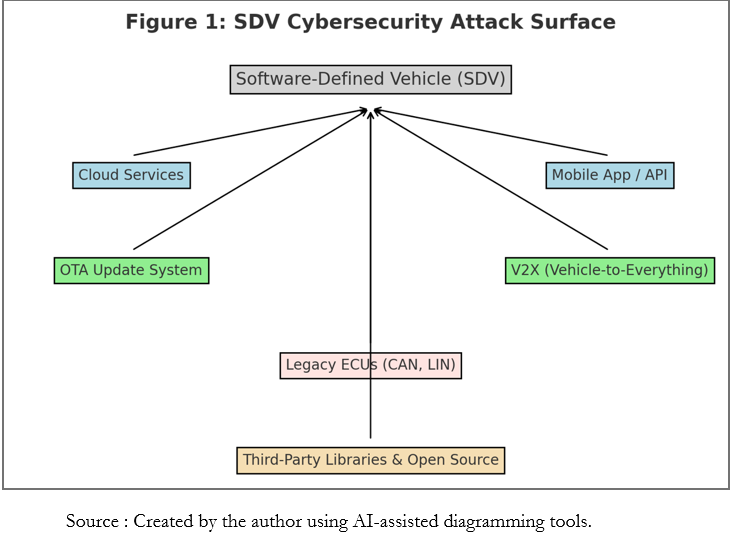
Emerging Countermeasures & Technologies
As SDVs become more interconnected and software-reliant, traditional perimeter-based security models fall short. Modern cybersecurity in SDVs must evolve into a multi-layered, adaptive defense framework that addresses threats from the silicon layer to the cloud. This section outlines the key countermeasures and technological approaches that OEMs and suppliers are increasingly adopting to secure the future of mobility.
Hardware Root of Trust and Secure Boot
Security must begin at the lowest levels of the vehicle architecture:
- Hardware Root of Trust (HRoT) establishes a secure identity at the silicon level and acts as an anchor for platform security.
- Secure Boot ensures that only authenticated and untampered firmware is executed during the startup sequence.
- Technologies such as Trusted Platform Modules (TPMs) and Hardware Security Modules (HSMs) are becoming standard in next-gen vehicle ECUs.
These measures protect against firmware tampering, supply chain attacks, and malware persistence.
AI-Driven Intrusion Detection & Prevention Systems
Given the complexity and high-speed nature of SDV data streams, AI-based intrusion detection systems (IDS) are being deployed across vehicle networks and back-end infrastructure. These systems:
- Monitor CAN, FlexRay, and Ethernet data traffic for deviations from learned behavior.
- Leverage unsupervised learning and anomaly detection to flag unknown threats, including zero-day exploits.
- Provide edge-based filtering and alerts, reducing latency in threat response.
Emerging research also explores federated learning models for cross-vehicle learning, where threat intelligence can be trained across a fleet without violating privacy.
Cryptography for In-Vehicle Communication
Traditional automotive protocols like CAN, LIN, and FlexRay lack built-in security mechanisms. Therefore, integrating cryptographic protocols is essential:
- Message Authentication Codes (MACs) and digital signatures ensure integrity and authenticity.
- Lightweight encryption techniques are tailored for resource-constrained ECUs.
- Time-triggered architectures are used to validate freshness and prevent replay attacks.
Cryptographic libraries must be automotive-grade and ISO 26262-compliant, as failure could impair functional safety systems.
Cloud API Hardening and Secure OTA Infrastructure
With SDVs frequently interacting with cloud services for OTA updates, telemetry, and diagnostics, API security becomes a critical control point.
- Employ OAuth2 and JWT for secure authentication and authorization.
- Use rate limiting, input validation, and payload sanitization to prevent injection and denial-of-service attacks.
- Implement API gateways with traffic inspection and anomaly detection capabilities.
Additionally, secure OTA solutions should adopt dual-bank firmware designs, encrypted payloads, rollback capabilities, and digital signature validation before deployment.
Blockchain and Trust-Based Architectures
To address the lack of trust in peer-to-peer SDV interactions, such as in V2X environments, researchers are exploring blockchain and distributed ledger technologies (DLT):
- Blockchain can ensure non-repudiation and tamper-evidence in message transactions.
- Smart contracts can define access control policies for critical resources.
- Lightweight blockchain frameworks like IOTA or Hyperledger Sawtooth are being evaluated for vehicle compatibility.
Trust-based mechanisms, including fuzzy logic, game theory, and behavior scoring, are proposed to detect insider threats and validate message credibility, especially in CAV ecosystems.
Digital Twin Integration for Cyber Risk Simulation
Advanced OEMs are exploring digital twin frameworks—virtual replicas of SDV systems that simulate real-world behavior and cyber threat scenarios:
- Simulations help test IDS efficacy, exploit paths, and protocol vulnerabilities without affecting live systems.
- Twins can model sensor spoofing, AI manipulation, and ECU compromise scenarios.
- Combined with cyber range environments, they offer a safe ground for training SOC teams and validating incident response playbooks.
Zero Trust Architecture (ZTA)
Borrowing from enterprise security, Zero Trust Architecture (ZTA) is being adapted for SDVs:
- All nodes—including ECUs, mobile apps, cloud servers, and V2X modules—are assumed untrusted until verified.
- ZTA mandates strong identity verification, micro-segmentation of networks, and least-privilege access policies.
- Combined with continuous telemetry, ZTA reduces lateral movement and mitigates supply chain exploitation.
Collaborative Industry Efforts
Cybersecurity cannot be solved in silos. Several collaborative efforts have gained momentum:
- Auto-ISAC (Information Sharing and Analysis Center) facilitates real-time threat intelligence exchange among OEMs and Tier-1s.
- The CAMP V2X Security Credential Management System (SCMS) project provides the foundation for secure V2X messaging.
- Open-source platforms such as Uptane for secure OTA updates are increasingly adopted for their transparency and auditability.
These collective efforts aim to reduce fragmentation and accelerate maturity in automotive cyber practices.
Regulatory & Standardization Landscape
Efforts like ISO/SAE 21434 and UNECE WP.29 have formalized the cybersecurity expectations for automotive manufacturers. However, adoption remains inconsistent across OEMs and geographies. Regulatory agencies must work closely with the auto industry to enforce compliance and encourage global harmonization.
Recommendations for Securing SDVs
1. Design security from Day One—adopt DevSecOps for embedded and backend systems.
2. Continuously monitor with behavior-based intrusion detection systems.
3. Mandate Software Bills of Materials (SBOM) and secure CI/CD pipelines.
4. Regular red-teaming and penetration tests on full vehicle stacks.
5. Invest in quantum-resistant cryptographic methods and AI-augmented defense.
Conclusion
SDVs represent the future of mobility, but they also pose unprecedented cybersecurity challenges. The convergence of vehicle systems with cloud infrastructure, AI, and third-party ecosystems requires a comprehensive, adaptable security posture. OEMs, Tier-1s, and regulators must work collaboratively to embed cybersecurity into the DNA of modern automotive platforms.
References
1. Rathore RS, Hewage C, Kaiwartya O, Lloret J. In-Vehicle Communication Cyber Security: Challenges and Solutions. Sensors, 2022.
2. Guan T, Han Y, Kang N, et al. An Overview of Vehicular Cybersecurity for Intelligent Connected Vehicles. Sustainability, 2022.
3. Mwanje MD, Kaiwartya O, et al. Cybersecurity Analysis of Connected Vehicles. IET Intell. Transp. Syst, 2024.
4. VicOne Automotive Threat Intelligence Team. The State of SDV Cybersecurity. Whitepaper, 2024.
5. Sureddi S. The Use and Impact of AI in Enhancing Automotive Cyber Protection. J. Artif Intell Mach Learn & Data Sci, 2024.